In this scheme, pairs of letters are encrypted, instead of single letters as in the case of simple substitution cipher.
In playfair cipher, initially a key table is created. The key table is a 5×5 grid of alphabets that acts as the key for encrypting the plaintext. Each of the 25 alphabets must be unique and one letter of the alphabet (usually J) is omitted from the table as we need only 25 alphabets instead of 26. If the plaintext contains J, then it is replaced by I.
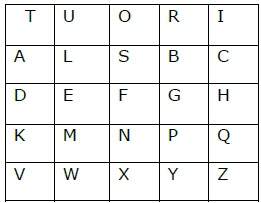
The sender and the receiver deicide on a particular key, say ‘tutorials’. In a key table, the first characters (going left to right) in the table is the phrase, excluding the duplicate letters. The rest of the table will be filled with the remaining letters of the alphabet, in natural order. The key table works out to be −
Process of Playfair Cipher
- First, a plaintext message is split into pairs of two letters (digraphs). If there is an odd number of letters, a Z is added to the last letter. Let us say we want to encrypt the message “hide money”. It will be written as −HI DE MO NE YZ
- The rules of encryption are −
- If both the letters are in the same column, take the letter below each one (going back to the top if at the bottom)
| T | U | O | R | I | ‘H’ and ‘I’ are in same column, hence take letter below them to replace. HI → QC |
| A | L | S | B | C | |
| D | E | F | G | H | |
| K | M | N | P | Q | |
| V | W | X | Y | Z |
- If both letters are in the same row, take the letter to the right of each one (going back to the left if at the farthest right)
| T | U | O | R | I | ‘D’ and ‘E’ are in same row, hence take letter to the right of them to replace. DE → EF |
| A | L | S | B | C | |
| D | E | F | G | H | |
| K | M | N | P | Q | |
| V | W | X | Y | Z |
- If neither of the preceding two rules are true, form a rectangle with the two letters and take the letters on the horizontal opposite corner of the rectangle.

Using these rules, the result of the encryption of ‘hide money’ with the key of ‘tutorials’ would be −
QC EF NU MF ZV
Decrypting the Playfair cipher is as simple as doing the same process in reverse. Receiver has the same key and can create the same key table, and then decrypt any messages made using that key.
Security Value
It is also a substitution cipher and is difficult to break compared to the simple substitution cipher. As in case of substitution cipher, cryptanalysis is possible on the Playfair cipher as well, however it would be against 625 possible pairs of letters (25x25 alphabets) instead of 26 different possible alphabets.
The Playfair cipher was used mainly to protect important, yet non-critical secrets, as it is quick to use and requires no special equipment.
No comments:
Post a Comment